Security
Security of the communications pathway to GENNECT Cloud
GENNECT One
Users are responsible for providing the communications pathway from GENNECT One to GENNECT Cloud.
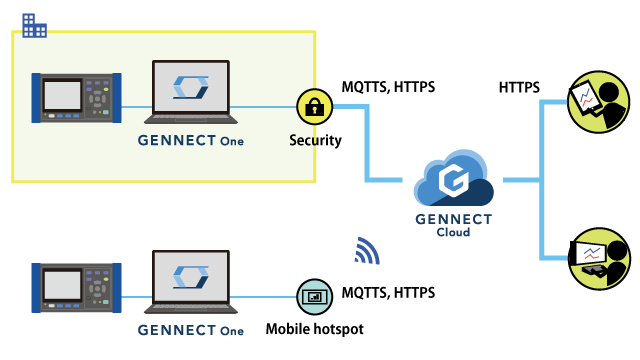
- If connecting from your internal LAN, you may need to change your company’s internal security policy.
- If connecting from outside your company, please provide a mobile hotspot or similar device.
- Communications between instruments and PCs: LAN
- Communications between PCs and GENNECT Cloud: User-provided, encrypted communications
- Log in to GENNECT Cloud and use remote measurement mode.
GENNECT Cross
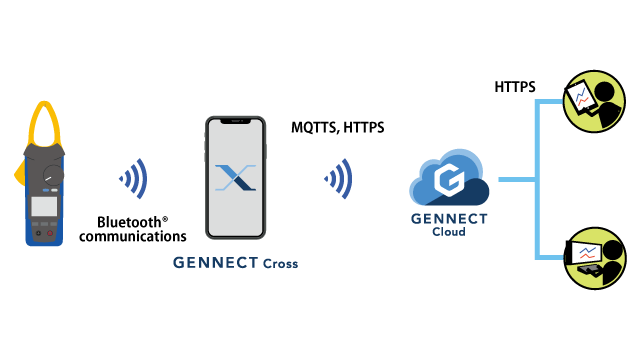
- Communications between instruments and smartphones/tablets: Bluetooth®Communications
- Communications between smartphones/tablets and GENNECT Cloud: User-provided, encrypted communications
- Log in to GENNECT Cloud and use the cloud monitor function.
Web browser
- Communications between PCs/smartphones/tablets and GENNECT Cloud: User-provided, encrypted communications
- Log in to GENNECT Cloud.
Two-factor authentication
Two-factor authentication can be configured in order to increase security when logging in.
If two-factor authentication has not been enabled, log in using your account ID, user ID, and password. If your login information comes into the possession of a third party, that individual could log in fraudulently and steal data.
If two-factor authentication using email has been enabled, users must enter an authentication code after entering their login information. A unique authentication code consisting of random characters is issued for each login and sent by email.
In other words, fraudulent logins are prevented because only users who can receive emails are able to obtain an authentication code.
Two-factor authentication can be configured to use either email or app authentication.